Hey fellow email marketers!
Today, we are going to continue our Inboxy blog series on email authentication by focusing on SPF Email Authentication.
Most quality email marketers are aware that email authentication is a critical aspect of modern email security. Authentication helps prevent email fraud and spoofing, which can lead to damaging consequences for individuals and organizations alike.

One widely used email authentication method is the Sender Policy Framework (SPF).
In this blog post, we will dive into the world of SPF, understand how it works, explore its benefits, learn how to implement it, and troubleshoot common issues.
Let’s demystify SPF email authentication and unlock its potential to enhance email security.
Why Do Email Marketers Need Email Authentication?
Email authentication is a process that verifies the authenticity of the sender’s email address and prevents unauthorized access.
Email authentication is important for several key reasons:
1. Prevents email fraud and spoofing
Email fraud and spoofing are common tactics used by cybercriminals to deceive recipients into revealing sensitive information, conducting fraudulent activities, or spreading malware.

Email authentication helps verify the authenticity of emails, ensuring that only legitimate emails from authorized senders are delivered to recipients’ inboxes and reducing the risk of falling victim to email scams.
2. Enhances email deliverability and reputation
Email authentication helps improve the deliverability of legitimate emails by establishing trust with recipient mail servers.
By using authentication methods such as SPF, DKIM, and DMARC, senders can demonstrate to email receivers that their emails are genuine, reducing the likelihood of being marked as spam or rejected.
3. Protects brand reputation and customer trust
Email fraud and spoofing can severely impact a brand’s reputation and erode customer trust. Unauthorized use of a brand’s name or domain in fraudulent emails can damage the brand’s reputation and result in financial losses, legal liabilities, and customer dissatisfaction.
4. Compliance with industry regulations and standards
Many industries have regulations and standards that require organizations to implement email authentication as part of their security measures.
For example, financial institutions, healthcare organizations, and government agencies may be required to comply with regulations such as the Gramm-Leach-Bliley Act (GLBA), Health Insurance Portability and Accountability Act (HIPAA), and Domain-based Message Authentication, Reporting, and Conformance (DMARC) for email authentication.
Compliance with these regulations helps organizations meet their legal and industry requirements and demonstrates their commitment to protecting sensitive information.
Implementing effective email authentication methods such as SPF, DKIM, and DMARC is essential for organizations to safeguard their email communications and maintain a secure and trustworthy email environment.
Understanding Sender Policy Framework (SPF) Email Authentication
So, how does SPF work?
SPF works by allowing domain owners to define a policy that specifies which mail servers are authorized to send emails on their behalf. When an email is received, the recipient’s mail server can check the SPF record of the sender’s domain to verify if the email is coming from an authorized source.

SPF records are published in the Domain Name System (DNS) and contain information about the authorized mail servers for a domain.
Implementing SPF Email Authentication
So, how do we implement SPF? Let’s get a quick step-by-step lesson:
To set up an accurate SPF record for your domain that includes all authorized sending domains, follow these simple steps.
Step 1: Gather IP addresses from mail servers used to send email
Organizations send mail from a variety of places, and this is reflected in the setup of your SPF, DKIM and DMARC protocols.
The first step to implement SPF is to identify which mail servers you will use to send email from your domain. You’ll start by making a list of all your mail servers and their IP addresses, and assess whether any of the following are used to send email on behalf of your organization:
- Your email service provider’s (ESP) mail server
- In-office mail server (e.g., Microsoft Exchange)
- Any other third-party mail server used to send email on behalf of your brand
- The mail server of your end users’ mailbox provider
If you’re unsure of what your IP addresses are, reach out to your IT System Administrator to compile a list of IP addresses your business uses.
Step 2: Create your SPF record
SPF is a protocol designed to restrict who can use an organization’s domain as the source of an email message. SPF blocks spammers and other attackers from sending email that appears to be from a legitimate organization.
SMTP (Simple Mail Transfer Protocol) does not place any restrictions on the source address for emails, so SPF defines a process for the domain owners to identify which IP addresses are authorized to forward email for their domains.
Here’s how to create your SPF record.
- Start with v=spf1 (version 1) tag and follow it with the IP addresses that are authorized to send mail. For example, v=spf1 ip4:1.2.3.4 ip4:2.3.4.5
- Using a third party to send email on behalf of the domain? In this case, you need to add an “include” statement in your SPF record (e.g., include:thirdparty.com) to designate that third party as a legitimate sender
- Once you have added all authorized IP addresses and include statements, end your record with an ~all or -all tag
- An ~all tag indicates a soft SPF fail while an -all tag indicates a hard SPF fail. In the eyes of the major mailbox providers ~all and -all will both result in SPF failure.
- SPF records cannot be over 255 characters in length and cannot include more than ten include statements, also known as “lookups.” Here’s an example of what your record might look like: v=spf1 ip4:1.2.3.4 ip4:2.3.4.5 include:thirdparty.com -all
- For your domains that do not send email, the SPF record will exclude any modifier with the exception of -all. Here’s an example record for a non-sending domain: v=spf1 –all
- You did it! You’ve created your SPF record. Let’s now get ready to publish it!
Step 3: Publish your SPF to DNS
Once you’ve crafted your SPF record, publish it as a TXT entry in your domain’s DNS settings. This will enable receiving mail servers to verify the authenticity of emails sent from your domain by checking against the published SPF record.
Step 4: Test!
You can test if your SPF was implemeneted correctly by using our free inbox placement test. See the exact breakdown of these 3 important technical configurations how they impact your email deliverability.
Troubleshooting SPF
Troubleshooting SPF can involve identifying and resolving issues related to SPF record errors, DNS configuration, and email delivery.
Here’s a more detailed overview of the SPF troubleshooting process:
SPF record errors: SPF records have a specific syntax and components that need to be correctly defined.

Common errors include:
- missing or incorrect mechanisms
- improperly formatted IP addresses or domain names, and
- incorrect use of qualifiers.
To troubleshoot SPF record errors, carefully review the SPF record for any syntax errors or incorrect information. Make sure that all authorized mail servers are correctly listed in the SPF record, and that the mechanisms and qualifiers are accurately defined.
DNS configuration issues: SPF records are published in the DNS, and any issues with DNS configuration can impact the effectiveness of SPF authentication.
To troubleshoot DNS configuration issues, ensure that the SPF record is correctly published in the DNS for the domain in question. Double-check the DNS settings to confirm that the SPF record is properly configured and accessible to recipient mail servers.
Email delivery issues: If legitimate emails are still being marked as spam or rejected, it could indicate issues with SPF authentication. To troubleshoot email delivery issues, review the SPF record and make sure that all authorized mail servers are listed.
Check for any discrepancies between the SPF record and the actual mail server configurations. If necessary, update the SPF record to accurately reflect the authorized mail servers.
Testing and monitoring: Regularly test and monitor the SPF authentication process to ensure its effectiveness.
Use SPF testing tools like Inboxy’s and services to verify that the SPF record is correctly published and that emails from authorized mail servers are passing SPF checks.
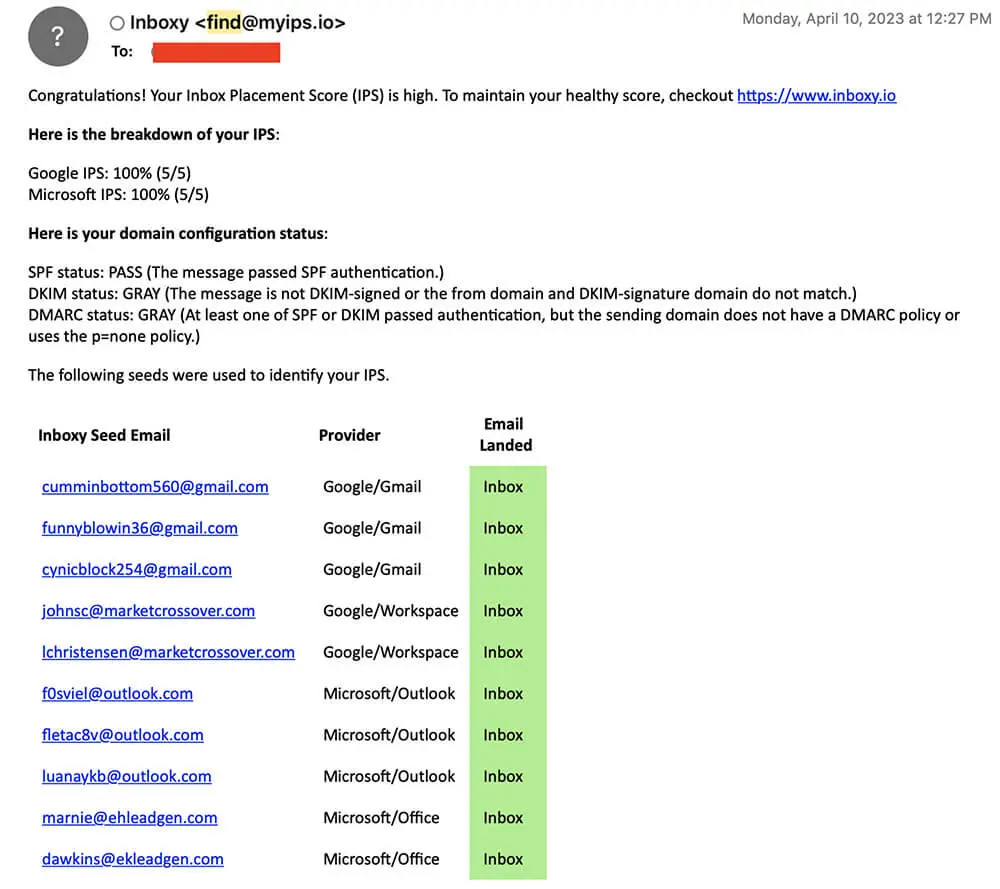
To get started, simply compose a new email message addressed to find@myips.io. The subject line should contain “report” followed by your domain name (e.g., “report example.com”).
There’s no need for any content in the body of the email. Once sent, you’ll receive a response containing valuable insights into your current SPF, DKIM, and DMARC configurations.
Seek assistance: If you encounter challenges during the SPF troubleshooting process, do not hesitate to seek assistance from your IT team, mail server provider, or SPF experts. They can provide guidance and expertise in resolving SPF-related issues and ensuring proper SPF implementation.
Remember to always follow best practices for SPF implementation, keep your SPF record up-to-date, and regularly monitor and test SPF authentication to maintain optimal email security.
Troubleshooting SPF may require attention to detail and technical expertise, but it is crucial in ensuring that SPF is effectively preventing email fraud and spoofing.
Conclusion
Understanding and implementing Sender Policy Framework (SPF) email authentication is vital for organizations and email marketers to enhance email security, prevent email fraud and spoofing, protect brand reputation and customer trust, and comply with industry regulations.
By creating SPF records, configuring DNS settings correctly, avoiding common mistakes, and following best practices, organizations can establish trust with recipient mail servers, ensure the authenticity of their emails, and reduce the risk of falling victim to email scams.
Implementing SPF alongside other email authentication methods such as DKIM and DMARC can provide even stronger protection against email fraud.
By taking proactive measures to implement SPF and other email authentication methods effectively, organizations can maintain a secure and trustworthy email environment, safeguard their brand reputation, and protect their valuable data and customers.
Learn more about Inboxy
Inboxy is the leading email warmup service that ensures that your emails are delivered to inboxes at nearly a 100% rate. Learn more about our service here!
